Last Updated
MapAttending IndieWebCamp SF
I am once again co-organizing and once again volunteering to handle the video for the intros, sessions and demos. This means I will be bringing the equipment to record the sessions, which will be ultimately available online. You can watch our last event, in Berlin Germany, here. The intros, demos, and keynote are not yet up, but I’ve added most of the sessions. You can see examples of those at the prior event in Brighton UK, available here.
IndieWebCamps are a great place to talk about creating or updating your own website and the technologies or ideas around it. The first day involves sessions, the topics for which are chosen by the attendees. The second day is when you build and demo something you built the previous day.
It is a fun event at a minimal cost. If you are in the area, why not stop by?
The IndieWebCamp San Francisco is a two day creatives workshop 2019-12-07…08 for anyone who wants to come discuss, brainstorm, or hack on any and all independent, distribute, local, offline, indieweb technologies for practical usable solutions to real world problems and social media.
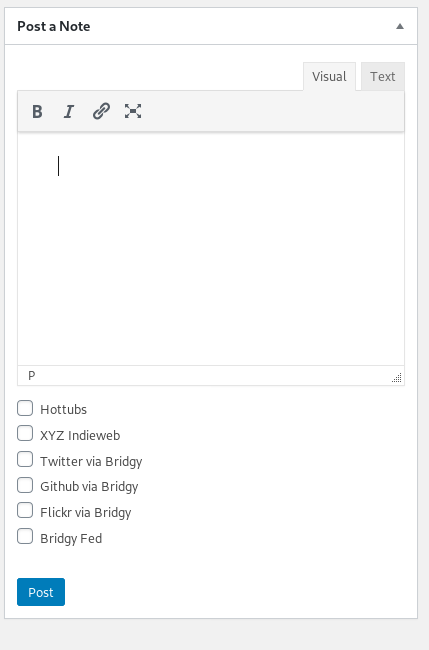 For IndieWebCamp Berlin 2 2019, I built this proof of concept feature in the WordPress Admin. It does actually work, but the functionality that enables the posting needs a lot more backend work before it will work properly.
For IndieWebCamp Berlin 2 2019, I built this proof of concept feature in the WordPress Admin. It does actually work, but the functionality that enables the posting needs a lot more backend work before it will work properly.
Problem is that the WordPress post endpoint does not allow you to set a taxonomy during post creation, so I need a custom endpoint. If I need one, it needs to be a bit more fleshed out so I can use it.
I considered modifying the Micropub endpoint to accept local queries and sending everything in Micropub, but a custom endpoint seems simpler for what is being done.